Hi, this is Sandra Henry-Stocker, author of the “Unix as a Second Language” blog on NetworkWorld.
In this Linux tip, we’ll take a quick look at apparmor. It’s a security module that runs by default on certain Linux systems – like newer Ubuntu and Debian. It’s notably different than SELinux and, in fact, the two security modules cannot run at the same time. Apparmor enforces restrictions using file system paths while SELinux applies security labels to objects. Think executables vs file system locations.
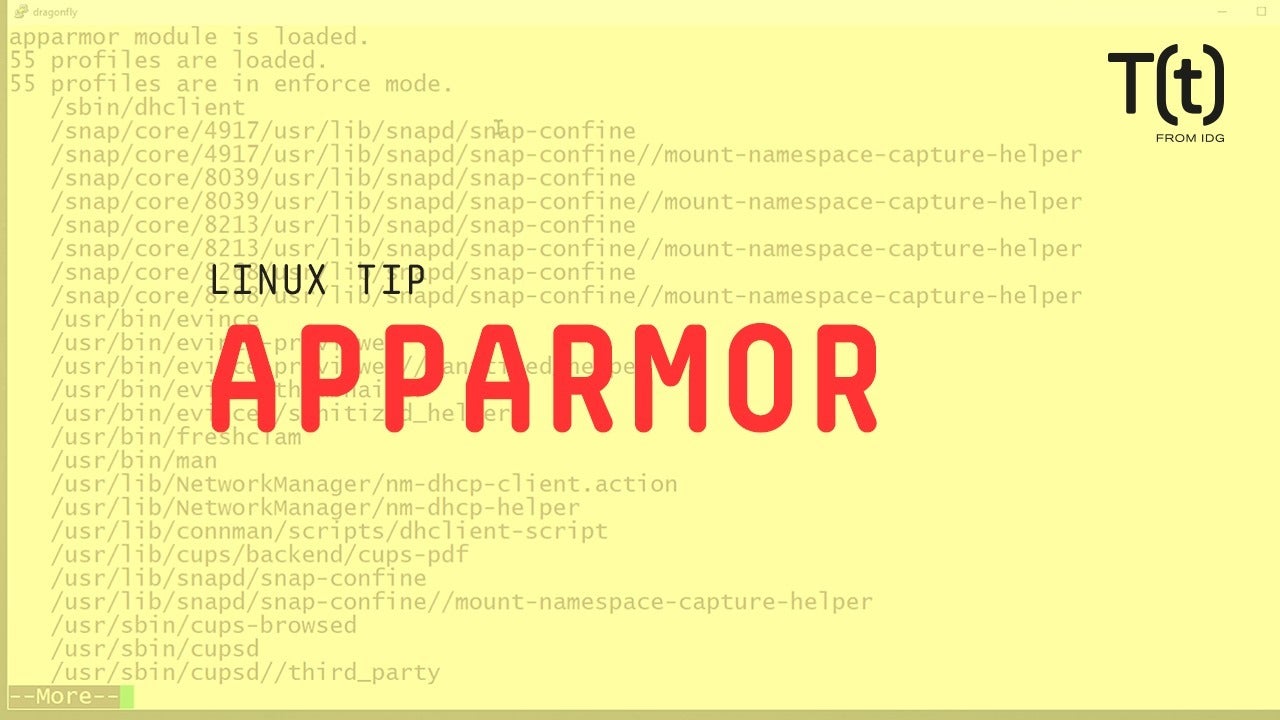
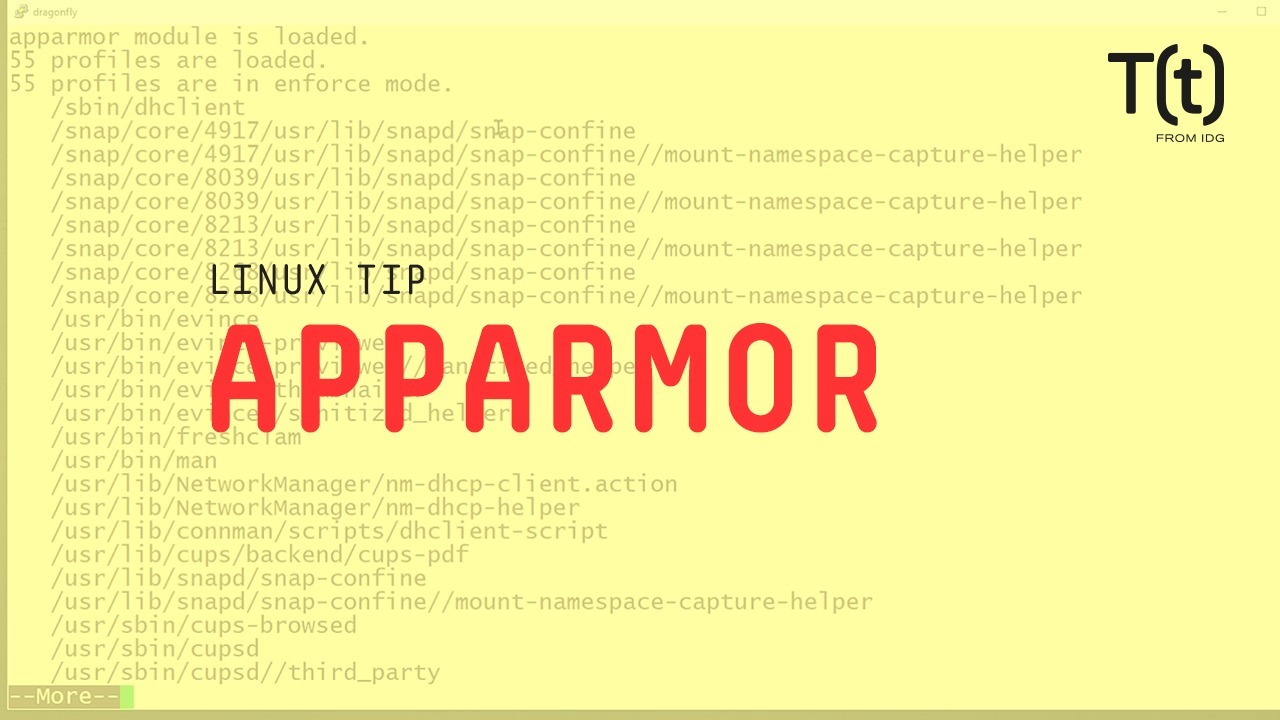
To determine if apparmor is operational on your system, use the apparmor_status command. You won’t find the command at all if apparmor is not installed.
If you see a lot of output like this, apparmor is running. This output also shows you how many security profiles are loaded and in “enforce mode” and how many are in “complain mode” – think working vs warning. It also shows many processes have profiles defined, how many are in enforce mode, how many are in complain mode and how many are unconfined but still have a profile.
The main point is that apparmor restricts processes/applications that might otherwise be exploited and it largely does this without requiring that you do anything to configure it, though application profiles, stored in /etc/apparmor.d, can be modified as needed.
$ ls /etc/apparmor.d | tail -5
usr.sbin.cups-browsed
usr.sbin.cupsd
usr.sbin.ippusbxd
usr.sbin.rsyslogd
usr.sbin.tcpdump
Notice how the file names reflect the executables’ paths.
That’s your Linux tip introduction to apparmor. If you have questions or would like to suggest a topic, please add a comment below. And don’t forget to subscribe to the IDG Tech(talk) channel on YouTube.
If you liked this video, please hit the like and share buttons. For more Linux tips, be sure to follow us on Facebook, YouTube and NetworkWorld.com.